In the evolving landscape of data enablement, the need to leverage data for driving efficiency, spurring innovation, and fostering collaboration has never been greater. This pursuit should be balanced with the escalating demands of information governance and privacy. As organizations delve into the intricacies of data utilization, the need for a robust and practical approach to anonymizing data emerges as a focal point. We explore the journey from evaluating a single dataset, to managing a pool of data, culminating in a system flow designed to produce consistently anonymized data, all underpinned by best practices aligned with international standard ISO/IEC 27559 De-identification Framework.
Readiness for international best practices
At the heart of responsible data management is the ISO/IEC 27559 standard, which provides a comprehensive framework for de-identifying personal data, including threat analysis, adversary testing, and governance of practices. This standard identifies and mitigates risks associated with anonymized or de-identified data and also establishes global best practices for data reuse and sharing. In a world where data about people is valued and responsibly treated as a protected asset, adhering to this standard ensures that organizations can responsibly leverage this data while maintaining public trust and upholding regulatory norms.
Understanding the breadth of international best practices is critical, differentiating between options and design parameters that will achieve alignment with key stakeholders and meet regulatory expectations. This approach transcends the confines of a single dataset, extending its applicability to pools of data and systems generating a flow of anonymized data (which we can call a data pipeline for short). This adaptability makes the approach to safely leveraging data a cornerstone for organizations aiming to meet international benchmarks in data security and privacy.
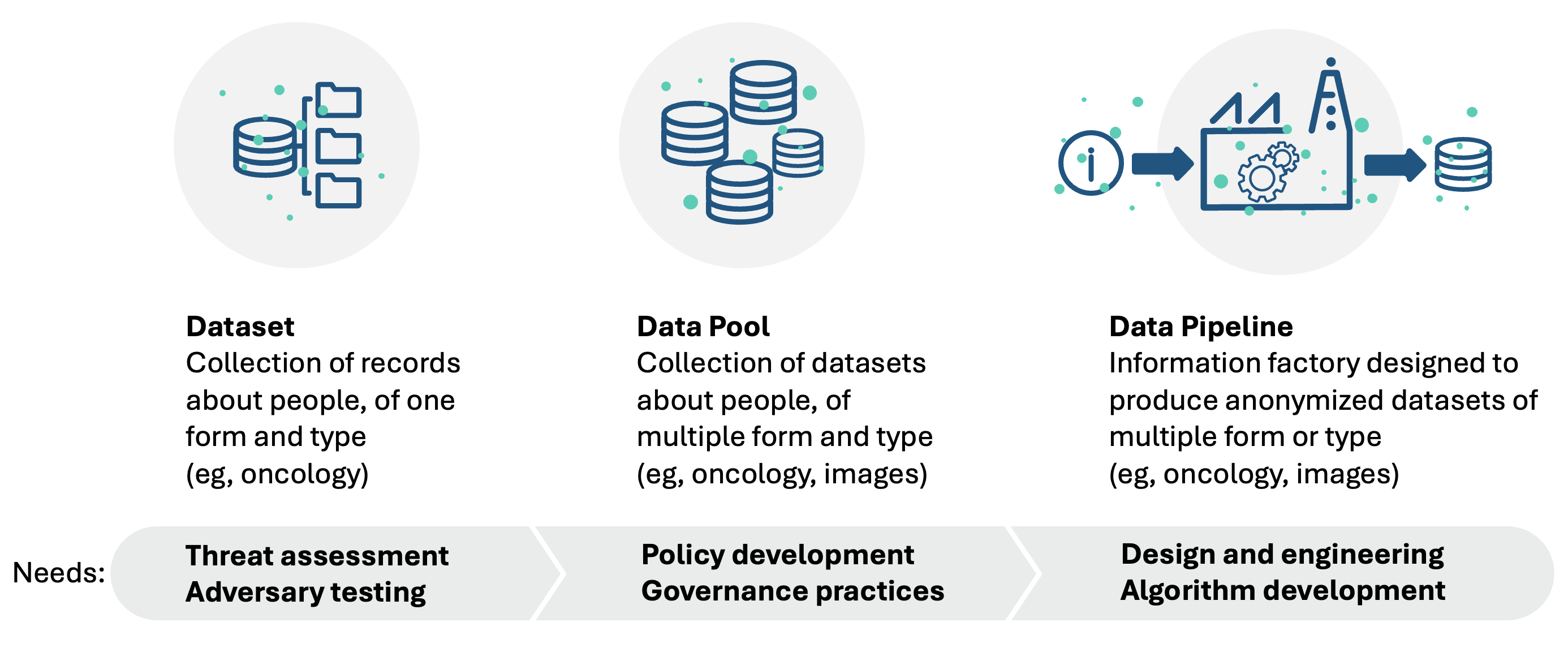
As shown in this diagram, as an organization collects more anonymized or de-identified datasets, the expectations outlined in international best practices will also increase. Evaluating a single dataset typically involves a third-party threat assessment (which we call re-identification risk determination) and adversary testing (also known as motivated intruder testing); evaluating a data pool, such as a data warehouse or data lake, will add the need for policy development and formal governance practices (specific to anonymized or de-identified data); evaluating or designing a data pipeline that produces such datasets will encompass all of the previous and more, since it could also involve more complex data flows and the creation of algorithms.
Preparing for a shifting regulatory landscape
With the advent of stringent enforcement mechanisms in new legislations such as USA state laws and the European Health Data Space (EHDS), the urgency to adhere to these practices is amplified. The alignment with global best practices in data reuse and sharing, outlined by the framework in ISO/IEC 27559 with implementation options described in regional guidance, is both a regulatory requirement and a distinct advantage. This standard and guidance serve as a yardstick against which data protection and privacy are evaluated for the effectiveness of anonymization and de-identification processes.
Think of international standard ISO/IEC 27559 as the scaffolding around which anonymization solutions can be built. However, other standards and guidance may also come into play depending on the scale of operations. For example, there may be a need to consider adherence to data protection and privacy legislation for platform or pipeline design for the lifecycle of data. Depending on how the resulting data is then used, this may also include emerging expectations for AI enablement, including risk and impact assessments, governance, and risk management in general.
Bridging the gap to best practices
By mapping your existing approach to ISO standards and guidance, we offer a clear pathway to best practices, ensuring that your organization is prepared for today’s challenges and is future-proofed against an evolving regulatory landscape. Through a detailed gap analysis, options summary, and the development of an implementation roadmap, our technical experts identify discrepancies and provide actionable insights to achieve alignment with international best practices and guidance.
Navigating the complex terrain of anonymized or de-identified data requires a intentional approach, one that balances the dual goals of leveraging data for organizational excellence and adhering to stringent privacy standards. Our design and engineering services, grounded in the ISO/IEC 27559 framework, as well as national and international guidance, offer a comprehensive solution that empowers your organization to achieve this balance, fostering responsible data reuse and sharing in the global arena.